BadUSB and the Hidden Microcontroller
BadUSB – what is it, and why is it scary? If you know something about microcontrollers and low-level electronics, the import of the recently-published BadUSB vulnerability is obvious and alarming. It destroys our nice little abstraction of external data storage being just a huge buffer of bytes, and reveals the microcontrollers and other control mechanisms underpinning it. And as it turns out, those control mechanisms have some properties that can turn them into a virtually unstoppable malware juggernaut.
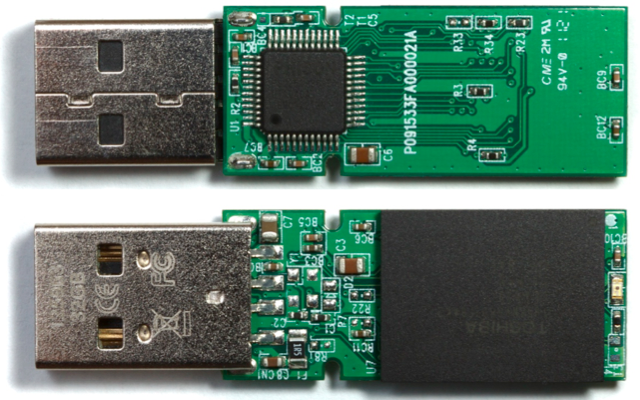
On every USB device from keyboard to thumb drives to web cameras, there’s a simple microcontroller that runs the hardware. It’s this microcontroller that actually talks to your PC, and processes keystrokes or fetches data from flash memory. Normally this microcontroller is invisible to the operating system and any programs running on the PC: they just send USB commands to the device, and get USB data back. The microcontroller is the invisible man in the middle, executing those USB commands.
Like your Arduino or any other microcontroller, the microcontroller on a USB device has its own simple control program called firmware. The firmware is authored by the USB device manufacturer, and is typically stored in a special non-volatile buffer in the microcontroller itself. But just like your Arduino, this firmware can be updated. And here’s where it gets scary.
A traditional piece of malware might scan your attached USB devices, looking for any that use a particular controller chip it knows how to infect. When it finds one, this malware could silently update the microcontroller firmware on that device. If the device is a USB thumb drive, the modified firmware might include a new behavior that does on-the-fly modification of every file retrieved from the thumb drive’s mass storage memory, attaching a virus. Boom! That thumb drive will now instantly infect any computer it’s plugged in to. But unlike a virus stored as a regular file in mass storage, it can’t be deleted. Erasing or reformatting the contents of the thumb drive will have no effect.
OK, that sounds bad. But maybe anti-virus programs could be upgraded to scan the firmware on attached USB devices and look for known evil USB firmware. Sounds good, but it’s not possible. The firmware of a USB device can typically only be read back with the help of that same firmware, if at all: A malicious firmware can spoof a legitimate one. For all practical purposes then, evil USB firmware is undetectable.
The range of possible exploits from evil USB firmware is very broad, and silently attaching a virus to every file retrieved from mass storage is just one example. Because the evil USB firmware can identify itself as a different type of device than it truly is, or even as a hub with multiple fictional devices, all sorts of crazy scenarios are possible. The researchers who first published the vulnerability described several possible exploits, including generating fake keyboard/mouse input, stealing passwords, redirecting network traffic, and even breaking out of a virtual machine.
At present, there appears to be very little that anyone can do to protect against this vulnerability, to detect it, or to remove it. A true fix would require a fundamental change to the way USB devices operate, and even then billions of older USB devices would remain vulnerable for years to come.
Read 1 comment and join the conversation1 Comment so far
Leave a reply. For customer support issues, please use the Customer Support link instead of writing comments.


Very helpful information. Thanks!